Penetration Testing Services
In today’s digital landscape, IT teams are constantly constructing, maintaining, and refining their network defenses against a relentless wave of internal and external threats. But how well do these defenses truly hold up? Understanding your vulnerabilities is the key to safeguarding your digital castle.
NetCloud Defence (NCD) goes beyond traditional testing. We take the time to truly understand your business and its unique security landscape. By adopting the perspective of a cunning attacker, we gain a multifaceted view, encompassing both the big picture and the intricate technical aspects of your systems. Leveraging pre-defined goals, we prioritize vulnerabilities, systematically targeting your weakest links and relentlessly probing until we identify those critical entry points that could lead to a complete system compromise and privileged access to sensitive information.
Our Vulnerability Assessment and Penetration Testing (VAPT) services employ a blended methodology, seamlessly integrating the efficiency of automated tools with the expertise of manual testing. We conduct safe and controlled attempts to gain privileged access to your firewalls, networks, devices, servers, Internet of Things (IoT) systems, web applications, and any other potential vulnerabilities. Once a vulnerability is successfully exploited, our security analysts will simulate a multi-stage attack, aiming to escalate their privileges and navigate deeper into your electronic infrastructure to access critical information.
This comprehensive approach offers an in-depth understanding of your security posture, empowering you to prioritize remediation efforts and fortify your defenses against real-world cyber threats. Partner with NCD and let us help you build a truly impregnable digital fortress.

NetCloud Defence is a worldwide CREST Accredited Penetration Testing service provider with CREST certified Penetration Testers and covering mainly Hong Kong and Southeast Asia region
Learn more about CREST and the benefits of engaging an accredited penetration testing provider
Our Penetration Testing Certifications
Why penetration testing with our Cybersecurity Consulting?
Our solutions deliver the security you need, maximizing your investment.
Identify Your Security Weaknesses
We uncover vulnerabilities across your entire digital landscape, from networks and applications to IoT devices, with internal, external, and simulated attack testing for complete security coverage.
Ensure Seamless
Compliance
Backed by decades of experience, our consultants can guide you through complex compliance requirements like PCI DSS, crafting and executing test plans that ensure effortless compliance.
Mitigate Human
Risk Factors
Modern cybercriminals recognize your employees as a key access point. We simulate real-world attacks, including phone scams, phishing emails, social media impersonations, and even physical intrusion attempts, to expose and address these vulnerabilities within your workforce.
Data-Driven Decisions for Security Remediation
We leave no stone unturned. From internal networks to mobile apps, we identify vulnerabilities across your entire technology stack, including wireless networks, IoT devices, and even simulated attacks through Red Team exercises.
Get Expert Guidance from Our Security Specialists
Partner with seasoned pen testers who see your defenses through an attacker’s eyes, leveraging years of experience to secure your organization from real-world threats.
Prioritize and Address
Security Risks
Our consultants will reveal your vulnerabilities, explain their real-world impact, and guide you in prioritizing effective remediation.
Uncover Hidden Vulnerabilities: The Power of Penetration Testing
Customized for Your Unique Security Landscape
Features
Details
Right-Sized Security Assessments
Standards-Based Solutions
Pretexting and Social Influence Techniques
External penetration tests
and applications exposed to the Internet.
Web application assessments
Social engineering
to an end-user system, including escalating privileges.
Types of Penetration Tests
Internal Penetration Testing
An external penetration test acts like a dress rehearsal for a cyberattack, mimicking how outside hackers might target your web applications, websites, and external servers. This helps identify vulnerabilities that could be exploited to gain unauthorized access from the internet.
External Penetration Testing
Building on external pen tests, internal tests simulate an attacker who’s already inside, perhaps through phishing or disgruntled employees. This exposes vulnerabilities they could exploit to move laterally, escalate privileges, or access sensitive data, highlighting the importance of strong internal security and employee awareness.
Thick-Client
Our experts go beyond the surface to identify vulnerabilities in your downloadable software, from the user interface to data transfer and server security. We perform an in-depth analysis to find and fix weaknesses before attackers do.
Web Applications
Our in-depth penetration testing scans your web applications, APIs, and services for vulnerabilities attackers could exploit. We leverage cutting-edge techniques to fortify your defenses against modern web threats.
Mobile Applications
We go beyond the surface to identify vulnerabilities specific to mobile devices, following industry standards like OWASP. This ensures your apps are fortified against the latest mobile threats.
The Digital Backbone
Uncover Hidden Weaknesses. Our expert ethical hackers will simulate real-world attacks on your network, IT infrastructure, cloud environment, and servers. This goes beyond awareness – we identify exploitable vulnerabilities before attackers do, and show you the impact they could have. We’ll also assess user adherence to security policies to ensure a holistic defense.
Active Directory (AD)
Our expert penetration testers secure your Microsoft Windows Active Directory by mimicking real-world attacker tactics. We pinpoint weaknesses in authentication, authorization, and access controls before they can be exploited, preventing privilege escalation and complete domain takeover.
What are the phases of pen testing?
Let’s walk through the stages of pen testing processes one by one:
Phase 1: Planning and Reconnaissance
This initial stage lays the groundwork for subsequent activity by defining goals and gathering intelligence. Cyber teams typically decide on:
– The scope of the pen test
– Objectives tailored to specific areas or systems
– Essential tools and techniques based on objectives
Moreover, this phase involves collecting data such as network and domain names, and mail server configurations, to tailor attacks more precisely.
Phase 2: Scanning
The next step harnesses automated tools to understand how target applications behave under various conditions:
– Static analysis evaluates code without executing it.
– Dynamic analysis runs code or applications to observe real-time behaviors.
Scanners evaluate how well apps and services uphold security in variable environments, providing essential insights into potential vulnerabilities.
Phase 3: Gaining Access
In this critical phase, penetration testers mimic cyber attacks to identify exploitable weaknesses using:
– Cross-site scripting
– SQL injection
– Backdoor creation
Testers seek not just entry points but aim to demonstrate potential data breaches or system hijacks, gaining a clear sense of possible real-world damage.
Phase 4: Maintaining Access
Advanced penetration tests simulate prolonged system intrusions to see if the vulnerability allows for persistent unauthorized access.
This is an especially insightful investigation considering the strategies used by actual cybercriminals who prefer undetected operations over long periods.
Phase 5: Analysis
Finally, all gathered information from previous phases come together here in the pen test analysis report. This detailed report helps stakeholders understand:
– Specific vulnerabilities
– Data compromised during the test
– Time spent within systems by pen testers
Finally, creating strategies for prioritizing remediation according to urgency helps to build resilience against actual threats and ensures continuous improvement in cybersecurity measures in the long term.
Our Penetration Testing Methodology
in the OWASP Testing Guide, Open Source Security Testing Methodology Manual (OSSTMM) and Penetration Testing Execution Standard (PTES).
01
Preparation
02
Recon
03
Mapping
04
Analysis and Reporting
05
Vulnerability Exploitation
06
Vulnerability Discovery
What Are We Testing During a Penetration Test?
is composed of three main phases explained below:
Active & Passive Reconnaissance
Information gathering about the target organization, as well as identify underlying components such as operating systems, running services, software versions, etc. The following is a non-inclusive list of items that will be tested to allow us to craft our attack in an informed fashion, elevating our probability of success:
– Open domain search
– DNS investigation
– Public information search (search engines, social networks, newsgroups, etc.)
– Network enumeration
– Port scanning, OS fingerprinting, and version scanning
– Firewall enumeration
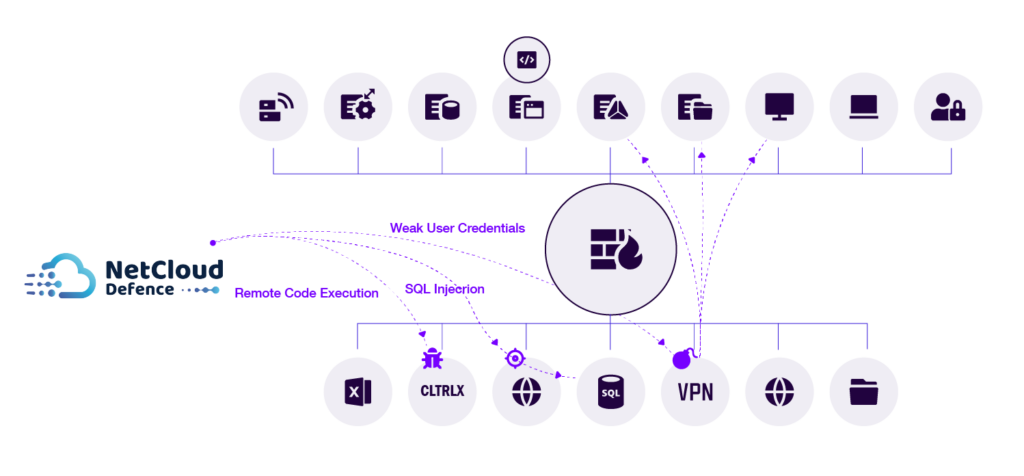
Vulnerability Identification
Assessment that consists of evaluating the information assets in scope against 80’000+ vulnerabilities and configuration checks, in addition to CWE/SANS TOP 25 Most Dangerous Software Errors and OWASP Top Ten vulnerabilities. wizlynx group uses several vulnerability scanners, as well as manual techniques, to test the many services that are reachable via the network such as SMTP, HTTP, FTP, SMB, SSH, SNMP, DNS, etc. The following vulnerability types can be identified (non-inclusive list):
Service-Side Exploitation
– Buffer overflow
– Code Injection
– Web Application exploitation
(XSS, SQLi, XXE, CSRF, LFI, RFI, and more)
Network Manipulation
& Exploitation
– ARP Spoofing
– HSRP/VRRP Man-In-The-Middle attack (MiTM)
– Routing Protocols MiTM
Identity & Authentication Weakness Exploitation
– Weak and guessable user credentials
Privilege Escalation
– Weak and guessable user credentials
Vulnerability Exploitation
Using a hybrid approach (automated and manual testing), our security analysts will attempt to gain privileged access to the target systems in a controlled manner by exploiting the identified vulnerabilities in previous phase “Vulnerability Identification”.
Supported Web Application Testing Approaches

Blackbox Web Application Penetration Test
Refers to testing a system without having specific knowledge of the inner workings of the information asset, no access to the source code, and no knowledge of the architecture. This approach closely mimics how an attacker typically approaches a web application at first. However, due to the lack of application knowledge, the uncovering of bugs and/or vulnerabilities can take significantly longer and may not provide a full view of the application’s security posture.

Greybox Web Application Penetration Test
Refers to testing the system while having some knowledge of the target asset. This knowledge is usually constrained to the URL of the application, as well as user credentials representing different user roles. Greybox testing allows focus and prioritized efforts based on superior knowledge of the target system. This increased knowledge can result in identifying more significant vulnerabilities, while putting in much less effort. Therefore, greybox testing can be a sensible approach to better simulate advantages attackers have, versus security professionals when assessing applications. Registered testing allows the penetration tester to fully assess the web application for potential vulnerabilities. Additionally, it allows the tester to verify any weaknesses in application authorization which could result in vertical and/or horizontal privilege escalation.

Whitebox Web Application Penetration Test
Refers to testing the system while having full knowledge of the target system. At wizlynx group, our whitebox penetration test is composed of a greybox test combined with a secure code review. Such assessments will provide a full understanding of the application and its infrastructure’s security posture.
What Security Advantages Do Penetration Tests Offer?
We deliver a comprehensive report designed for both technical and non-technical audiences.
This report equips you with a prioritized risk list for C-level decision-making, detailed results with evidence for remediation,
and a comparison of your security posture against industry standards. We’ll even present the findings and discuss recommendations,
ensuring you have a clear roadmap to fortify your defenses against evolving threats.
FAQ
Let’s get in touch
We’d love to help.





