What Is a Security Operations Center?
Imagine a central command center for your organization's security. That's the Security Operation Center (SOC). It combines skilled analysts, advanced tools, and well-defined procedures to constantly monitor your defenses. This vigilance helps prevent attacks, detect threats early on, analyze their nature, and swiftly respond to any security incidents. Ultimately, the SOC works tirelessly to improve your overall security posture.
The SOC acts as your security nerve center, constantly gathering data from every corner of your IT infrastructure – networks, devices, applications, and data storage – regardless of location. This comprehensive view is crucial in today's complex threat landscape, as advanced attacks often rely on scattered clues. Essentially, the SOC is where all security events from your monitored systems converge. Here, analysts analyze each event and determine the most effective response, ensuring a swift and coordinated defense against cyber threats.

SOC
GOIP Group x NetCloud Defence keeps your company safe around the clock. Our team of cybersecurity professionals acts as your 24/7 security watchtower, leveraging advanced security monitoring to detect threats and a comprehensive incident response plan to ensure a swift and effective response, keeping your business secure.
In today's digital world, every company is a target. GOIP Group with NetCloud Defence offers a powerful, all-encompassing security solution with a Security Operations Center (SOC) at its core. This SOC acts as your 24/7 security watchtower, combining advanced threat detection with a team of cybersecurity professionals to keep your business safe and running smoothly, so you can focus on what you do best.
GOIP Group x NetCloud Defence provides peace of mind with our 24/7 Security Operations Center (SOC) service. Our team of security experts acts as your virtual security watchtower, continuously monitoring real-time data and traffic across all your systems and devices. This allows them to identify and neutralize potential threats before they disrupt your business, keeping you safe and focused on what matters most.
What does a SOC do?
A high-functioning Security Operations Center (SOC) acts as your organization's 24/7 security war room. This elite team combines cutting-edge technology with deep security expertise to continuously monitor your entire network. This allows for real-time incident response, where threats are neutralized before they can cause damage. The SOC also drives ongoing security improvements, proactively identifying and patching vulnerabilities to keep your defenses ahead of evolving threats. In short, a high-functioning SOC provides an impenetrable shield against cyberattacks, giving you peace of mind and allowing you to focus on your core business.
Our service provides 24/7 proactive monitoring of your networks, hardware, and software. We act as your virtual security guard, constantly scanning for threats and breaches. This vigilance allows us to neutralize threats before they can disrupt your business. Plus, our team of experts is always on hand to respond swiftly to any incidents, minimizing damage and ensuring business continuity. This comprehensive approach gives you the peace of mind to focus on what matters most – running your business.
Our security team speaks fluent "security tool"—including third-party ones—for faster troubleshooting and resolution.
Monitoring and managing of firewall and intrusion prevention systems.
Scanning and remediation of antivirus, malware and ransomware solutions.
Email, voice and video traffic management.
Patch management and whitelisting.
Deep analysis of security log data from various sources.
Analysis, investigation and documentation of security trends.
Investigation of security breaches to understand the root cause of attacks and prevent future breaches.
Enforcement of security policies and procedures.
Backup, storage and recovery.
While it continuously monitors networks and devices for anomalies, collecting data and generating alerts, its true power lies in proactive threat prevention.
A watchful eye is only half the battle. While the SOC tirelessly monitors for threats, their true power lies in relentless prevention. They become proactive hunters, identifying weaknesses within your systems (through vulnerability analysis) and mimicking real-world attacks (penetration testing) to find loopholes. They're also security scholars, constantly researching the latest threats and gathering intel. Additionally, they analyze your security setup, ensuring you have the right tools and optimize your defenses. So even during calm periods, the SOC is relentlessly working to fortify your defenses and stay ahead of evolving threats.
Who works in a SOC?
The SOC is staffed with highly skilled analysts and engineers, overseen by supervisors who keep the operation running seamlessly. These professionals are trained specifically to handle security threats. They not only wield a wide arsenal of security tools but also possess the knowledge and procedures to swiftly respond and contain any security breach, ensuring your infrastructure remains secure.
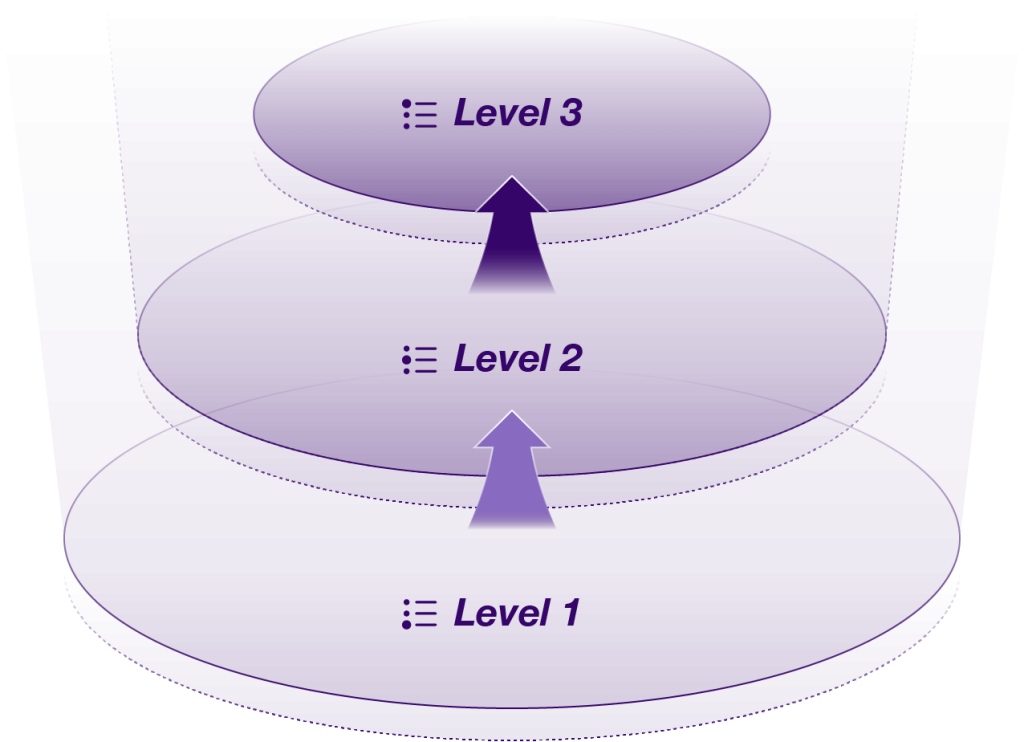
The best SOCs leverage a team with a rich tapestry of skills and experience. This ensures they can effectively manage security challenges at every level. These highly trained professionals work together seamlessly, constantly monitoring, analyzing, and responding to threats, keeping your organization safe from cyberattacks.
Level 3: At the core of your SOC lies a team of highly skilled security analysts. They act as your digital detectives, wielding advanced tools to continuously hunt for vulnerabilities within your network. Their expertise goes beyond detection – they analyze weaknesses and recommend proactive measures to strengthen your overall security posture. This elite team ensures your organization remains a step ahead of evolving cyber threats.
Level 2: When threats are detected, your SOC’s rapid response team springs into action. With their deep expertise, they quickly pinpoint the source of the attack and take decisive steps to contain it. Following established protocols, they swiftly remediate the issue, minimize any damage, and flag potential complications for further investigation. This ensures the fastest possible recovery and helps prevent future breaches.
Level 1: These security professionals act as your front line of defense. They continuously monitor for security alerts, swiftly assessing their severity and urgency. Equipped with the latest tools, they prioritize threats and efficiently manage the initial stages of incident response, ensuring timely escalation to more specialized teams when necessary. Their vigilance is key to containing threats before they can disrupt your operations.
GOIP Group x NetCloud Defence Solutions
We offer flexible, managed and co-sourced Security Operations Center (SOC) services, partnering with boards and collaborating closely with your security team for a comprehensive defense against cyber threats.
Get a custom-fit security shield for your business. We offer flexible, on-site or remote SOC services tailored to your specific needs.
Security Operations Center (SOC) goes beyond geographical boundaries. Our "connected execution" approach leverages a team of cyber experts across APAC, including Hong Kong and Malaysia. This global network, combined with cutting-edge technology like cloud-native security analytics, automation, and threat intelligence, empowers us to deliver professional, location-independent security operations for your organization.
A global network of specialized cybersecurity teams unites to deliver world-class, custom-fit security solutions, ensuring consistent protection across regions with local support on-demand.
Our adaptable security solutions seamlessly adjust as your business expands. This allows you to transform your cyber operations, proactively reduce risk exposure, and focus on growth with complete confidence.
Our deep expertise in managed security services translates into actionable insights and recommendations, empowering you to make informed decisions about your organization’s security posture.
Our extensive experience translates into a proactive approach, leveraging lessons learned to identify and avoid potential security roadblocks for your organization.
Our deep understanding translates into relevant security insights and specialized advice on leading practices, keeping you ahead of industry-specific threats.
We combine onshore and offshore resources for optimal client coverage, ensuring knowledge transfer builds your team’s internal security capabilities.
Our innovative phase-driven structure maximizes efficiency with 24/7 coverage, surpassing the limitations of a traditional onshore-offshore model.
Our proven approach simplifies security: enhanced automation streamlines processes and delivers robust protection for your organization.
Our deployment accelerators minimize setup time, ensuring a smooth and rapid transition to a state of optimal security.
Managed Services
Backup
We offer flexible data recovery options, allowing you to restore individual files or entire systems based on your specific needs, all with customizable retention timeframes for complete peace of mind.
Compliance and Security
Our multi-layered security approach leverages cutting-edge technology to safeguard your data and streamline continuous compliance, ensuring peace of mind on both security and regulatory fronts.
Disaster Recovery
Real-time data replication and seamless failover between sites ensure your systems stay up and running, minimizing downtime and maximizing operational continuity.
Network Access
Our services accelerate application delivery while simultaneously fortifying your security posture, giving you the best of both worlds: faster deployments and robust protection.
Storage
We offer a flexible solution for both long-term archival and short-term data storage, maximizing value and streamlining your data management.
Edge
A fully managed platform delivering on-demand computing power exactly where you need it, for a seamless and scalable cloud-like experience at the edge.
What GOIP Group x NetCloud Defence can provide?
Stay ahead of cyber threats with industry-leading intelligence and a mature 24/7 SOC.
Our experts leverage cutting-edge knowledge to proactively hunt threats, engineer security content, and fuse threat data, delivering a comprehensive response system that keeps your organization secure.
Comprehensive Threat
Prevention, Detection And Response
LMNTRIX XDR
Block endpoint, network, cloud and mobile attacks with a proven, lightweight next-gen agent, NETWORK sensors and APIs
NGAV, EDR, Mobile Threat Defense, Identity
NDR + Network Forensics + SIEM
Cloud Security (CSPM,CDR,EP)
Machine & Underground Intelligence
Full Visibility & ML-Driven Detection
Find stealthy threats with the solution that achieved the best combined MITRE ATT&CK detection & protection scores
Machine Learning and Analytics
Correlation, IOC & BIOC Rules
Rogue Device Discovery & Asset Management
Vulnerability Assessment
Accelerated Investigations
Quickly analyze attacks by grouping alerts into incidents and viewing rich investigate context
Incident Management
Root Cause Analysis & Cross-Data Insights
Live Terminal for Direct Endpoint Access
Advanced Threat Hunting
Uncover hidden threats with a powerful Query DSL querying language
XQL Query Language
Integrated Threat Intelligence
Active Threat Hunting
Coordinated Response
Swiftly contain fast moving threats across key enforcement points
Search and Destroy
Script Execution
File Block, Quarantine, Removal, Device Isolation
Automatic Containment Across Network & Cloud
Benefit from connected expertise of Security Operation Center (SOC) professionals
Safeguard your entire operation:
We offer comprehensive protection for both your IT and OT infrastructure, keeping you secure from malicious attacks.
Identify vulnerabilities leading to data breaches
Detect and response to cybersecurity incidents
Ensure that cybersecurity tools are healthy and used in efficient and cost effective way
Proactively discover ongoing breaches and be prepared for major incidents
Efficiently manage identification and remediation of vulnerabilities and security exceptions for them
Prepare well to successfully manage malware crisis
Develop and adapt detection mechanisms to emerging threats and improve incident response
Keep the information assets well protected in ever changing IT environment
Frequently asked questions about
GOIP Group x NetCloud Defence SOC:
What is a SOC?
A Security Operations Center (SOC) is a command center with cyber security professionals that continually monitor and enhance an organization’s security capabilities while detecting, analyzing, and responding to cybersecurity incidents and taking preventative measures in order to protect the company from cyber-attacks.
How does a SOC work?
These cybersecurity experts, armed with advanced technology and proven security procedures, work 24/7 to detect and swiftly respond to any cyber threats targeting your company.
What does a Security Operations Center do?
A SOC works 24/7 to ensure the safety of your company against cyber threats. A SOC monitors all Internet traffic, the internal network infrastructure, desktops, servers, endpoint devices, databases, applications, IoT devices and other systems in your company in order to identify potential security incidents.
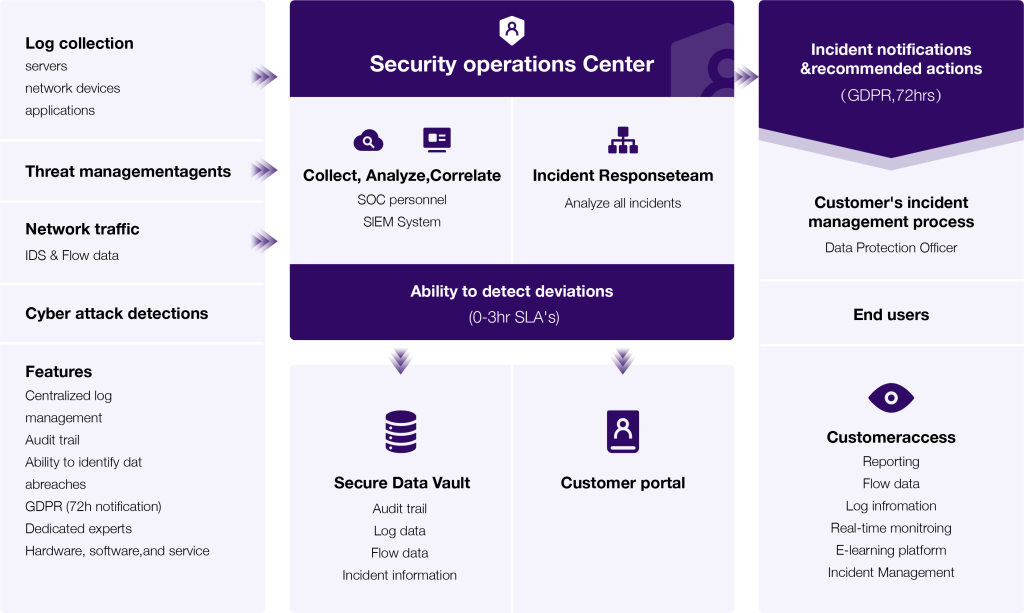
By combining a range of advanced tools and the knowledge of our experienced cybersecurity professionals, the NetNordic Security Operations Center can perform all these vital functions:
• Threat hunting.
• Management and maintenance of security devices.
• Risk-based vulnerability management (special prioritization of patch niches).
• Handling security incidents, including malicious analysis and forensic investigations.
• Management of threat information (intake, production, data security and dissemination).
• Development of data and measurement values for compliance reporting / management.
Monitor data, detect incidents, investigate and give out warnings and react accordingly.
What is a SIEM?
– Security Information and Event Management software.
SIEM stands for security information and event management and provides organizations with next-generation detection, analytics, and response.
NetNordic offers a centralized Security Information and Event Management (SIEM) system. The system monitors the customer’s information systems and networks, and issues alerts when it detects abnormal events or chains of events. The system of is comprised of components used for machine learning, analysis of globally collected threat data, correlation systems and threat assessment.
NetNordic SIEM enables a full view for our SOC-customers and allows them to view different components, build reports and follow real-time log data.
SOC vs SIEM- what's the difference?
A SIEM and a SOC complement each other – the SIEM allows for log data analysis and collection, while the SOC consists of people, processes and technology designed to deal with security events picked up from the SIEM.
Let's get in touch
Questions about GOIP Group x NetCloud Defence solutions?
We’d love to help.
Secure Today For A Safe Tomorrow
Safeguard people, Datd and infrastructure
NetCloud Defence
NetCloud Defence is a leading provider ofcybersecurity services, focusing on cross-bordersecurity for critical infrastructure. Our innovativesolutions include Software-as-a-Service (Saas)platforms, Direct Internet Access(DlA), and DataCenter Interconnect (Dcl)
Company
Contact Us
unit 03-06 27/F metropolis tower,6-10 metropolis drive,hung hom,kowloon
Monday-friday9:00 a.m.-6:00p.m.
info@ncdefence.com
+852 2138 9338




@Netcloud Defence 2024. All Rights Reserved.
